With the widespread use of technology across all industries, the chances of cyber attacks on systems are increasing day by day, and the automotive industry isn’t exempt from that; hence, the need for automotive Cybersecurity is felt. Cybersecurity is a significant concern because modern cars rely heavily on software and technology, and their utility is entirely dependent on them and a minor issue might lead to their failure. The Rockwell Automation Report released an annual report in 2024 that reported that automotive manufacturers considered Cybersecurity a significant risk. This is due to the fact that there has been quite an increase in the high profile data breaches with the inclusion of technology which eventually calls for effective solutions.
What is Automotive Cybersecurity?
Automotive Cybersecurity refers to the measures and technologies taken to protect online car inventory management system, websites and their systems from digital threats, ensuring the safety of the vehicles, their passengers, and consumer data. So in simple terms, it primarily protects vehicles from cyber threats such as hacking, unauthorized access, and malicious activities. The expanding automotive cybersecurity industry is a testament to the demand of businesses and manufacturers to look for solutions in the space.
The automotive cybersecurity market is estimated to be around $1 billion in the US alone, and it’s projected to shoot up to approximately $17 billion worldwide by 2032. North America is expected to play a pivotal role in this growth.

What are the Cybersecurity Protection Methods?
In addition to pre-defined solutions, researchers are now working on vehicle cybersecurity. The security layers of the protection techniques vary but are but are broadly divided into a few principal approaches and strategies. They mainly include encryption, authentication, intrusion detection systems, and secure communication protocols.
1) Network Security
The phrase essentially refers to safeguarding internal communications and contact with external systems in an automotive context. So, the network security is fully secured when the data is transferred without delay and is not susceptible to unauthorized access. The two major components are firewalls, which act as a barrier and block such vulnerabilities. Secondly, intrusion detection systems, or IDSs, come into action whenever a security breach occurs in some way, and firewalls cannot stop it. These are deployed to detect unauthorized attempts to access data or abnormal data flows.
2) Cybersecurity of firmware updates
Technology demands upgradation periodically, and the same applies to these vehicles, whether autonomous or electrical. It is an area of potential risk, as while updating the system, there are chances of some malicious software being installed on the vehicle’s system. This is generally avoided by using an encrypted model, which is made so that it cannot be intercepted, and the over-the-air updates are done through secure communication channels with the application of certificates and keys.
3) The Vehicle Research and Test Center, Ohio
The Vehicle Research and Test Center (VRTC) in East Liberty, Ohio, is a significant step towards conducting in-house Cybersecurity for automotive research and identifying potential vulnerabilities in these systems. Their approach is highly cooperative, working on new technology and detecting and mitigating risks, and to ensure the best possible results, they actively collaborate with the stakeholders in the industry like the cybersecurity automakers, lawmakers, and industry professionals, fostering on-the-ground implementation and seeking advice and reviews.
4) V2V Communication
Vehicle-to-vehicle (V2V) communication is a crucial feature of self-driving cars, enabling them to exchange information about their direction, position, and speed with the others cars in their close proximity. This helps in avoiding any accidents or disasters. And therefore, developing and continuously enhancing a reliable V2V communication parser is necessary as a false interpretation might incur serious consequences. The system must be secure, robust, and reliable to ensure the safety of all road users.
5) Cybersecurity considerations for heavy vehicles
There has been quite a similarity with passenger cars. Both rely on automotive software updates and network security and adhere to automotive cybersecurity regulations like Automotive Cybersecurity ISO 21434, which lays down guidelines for increasing the efficiency and lifetime of these vehicles. However, the difference comes when we talk about the systems, which are much more complicated and require an extra layer of security in fleet management.
Use Cases of Automotive Cyber Security
Technology is developing far more quickly in the US than in other parts of the world since the US is leading the world in the race for autonomous vehicles, cyber security, and other automotive engineering domains. So, applications increase because of technological changes and industry rules and compliances, which determine how the implementation will be done. The major trend is increasing demand for cloud-based applications, and there is also a rising demand for V2X-equipped vehicles, which eventually leads to a growing chart of connected vehicles.
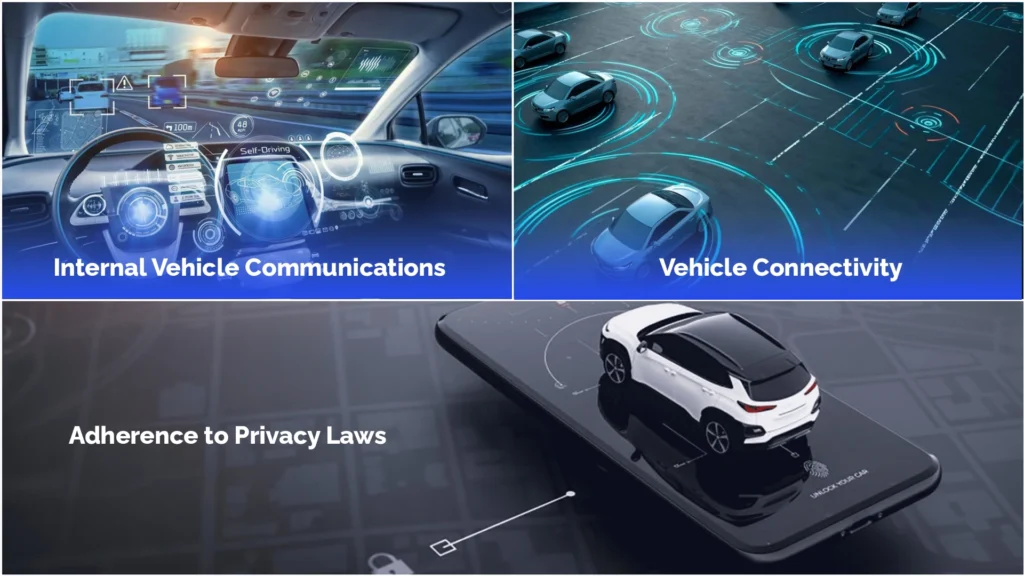
Let’s know about a few significant applications:
1) Internal Vehicle Communications
As earlier mentioned, IVC is necessary for the smooth functioning of the automobile. The National Highway Traffic Safety Administration (NHTSA) and other regulatory bodies emphasize secure communication between electronic control units (ECUs) to prevent hacking incidents that could compromise vehicle and passenger safety.
2) Vehicle Connectivity
Everyone wants entertainment on drives. This is only possible if the vehicles have good connectivity, mostly Bluetooth, and access to location services, especially electric cars.
3) Adherence to Privacy Laws
Privacy should not be compromised; in today’s era, it is like a right. Acts like the California Consumer Privacy Act (CCPA) emphasize the protection of personal data collected by vehicles. The onus is on automakers and technology providers to safeguard user information to comply with the laws and avoid any trouble in the future.
What are the Services Offered for Vehicle Cybersecurity?
To counter cyber threats and safeguard data for the smooth operations of automobiles, companies provide several services for vehicle cybersecurity. It depends on what kind of service is necessary for our systems. These services are crucial as vehicles become more connected and autonomous, introducing new vulnerabilities and risks.
1) Threat Detection and Prevention
As discussed earlier, Threat Detection and Prevention include firewall protection and an intrusion detection system, the first prevention layer when automotives are prone to attacks.
2) Security Testing and Assessment
This involves conducting security checks regularly to determine whether any vulnerabilities have gone unnoticed. Security patch updates are also included, and you will be kept updated on any potential vulnerabilities in the future.
3) Software and Firmware Management
OTA updates are crucial for patching vulnerabilities and adding new features without requiring physical access to the vehicle, which avoids a big hassle for the owner—similarly, the implementation of these techniques .
4) Real-time monitoring
It involves implementing mechanisms to check for possible cyber attacks. Similarly, anomaly detection tool leverages AI as well as machine learning to detect anomalies, i.e., unusual activity that looks suspicious and might be a cyberattack.
Advantages of Auto-Cybersecurity
Since the services used are quite beneficial in eliminating most of the cyber security threats, the advantages are very self-explanatory. Let’s have a look at the few major advantages that increase the importance of these services in today’s digital world.
1) Whether it is protection against cyber attacks, prevention of unauthorized access, or data protection, its most significant advantage leads to its demand.
2) It ensured compliance with automotive cybersecurity standards while protecting user data privacy and safety.
3) Secure on-board and off-board communication and secure boot regularly.
4) Regular maintenance also avoids losses incurred by data breaches and prepares for future threats.
5) Also, it maintains a certain level of confidentiality and is a trust-building factor for consumers.
6) Intrusion detection and intrusion prevention systems.
7) Cryptographic processes and management of cryptographic materials like certificates and keys.
How Do You Test Automotive Cybersecurity?
So validating and testing automotive cybersecurity requires connectivity gateways, a test management server, a reconnaissance and fuzzing server, and a library of known vulnerabilities and threats. Some tests are needed to check whether the steps taken are influential.
| Testing Method | Description |
| Risk assessment and threat modeling | Identify potential threats and vulnerabilities and assess their impact on the vehicle. Evaluate the impact of different types of cyber attacks. |
| Penetration testing and vulnerability scanning | Simulate cyberattacks to identify security weaknesses and use tools to scan for vulnerabilities. |
| Firmware, software, and hardware testing | Analyze the code for vulnerabilities, and test the hardware for physical and security flaws. |
Cybersecurity Best Practices for Modern Vehicles
The Cybersecurity best practices actually leverage agency research, industry voluntary standards, and learnings from motor vehicle cybersecurity research over the past several years and then implement them accordingly.
Some essential methods must be used religiously to eliminate cyber threats or potential risks and achieve the best possible results. These are implemented in different stages to maximize their impact and minimize the cyber threats faced.
1) Risk Assessment and Management
a) Identify Threats
To identify and prioritize risks and solve existing vulnerabilities.
b) Assessment and Analysis
Assess the potential impact of different types of cyberattacks on vehicle safety and operations.
2) Security by Design
a) Integrated Security
Embed security features into vehicle system design and development processes.
b) Lifecycle
Ensure security measures are maintained to increase the vehicle’s lifespan.
3) Collaboration and Information Sharing
a) Industry Collaboration
Gather a community and organize industry forums and initiatives to share information on threats and vulnerabilities.

b)Setting up conferences
To establish an ecosystem where collaboration and talks can be done on how to solve cyber threats.
4) Incident Response
a) Incident Response Plans
Layout a plan to tackle and neutralize cybersecurity attacks.
b) Regular Drills
Conduct regular drills and exercises to test the effectiveness of these response plans.
5) Awareness and Training
a) Employee Training
To train and spread awareness among employees about cybersecurity and make them technically equipped with the necessary skills.
b) Stakeholder Engagement
Engage with suppliers and other stakeholders to ensure they also implement best cybersecurity practices.
6) Continuous monitoring and improvement
a) Real-Time Monitoring
Implement a real-time system that monitors automobiles and assesses cyber threats.
b) Feedback Loop
Establish a feedback loop to make improvements periodically and eliminate cybersecurity threats and vulnerabilities.
Top Automotive Cybersecurity Companies
Considering the increasing cybersecurity concerns, the market has enough space to have more and more organizations catering to them. However, a few major ones have worked tremendously in the field of cybersecurity in the automotive industry. Let’s have a look at a few of them:
| Auto CyberSecurity Companies | Features |
| Harman | It is a subsidiary of Samsung and offers IDS solutions for Secure Comms & OTA updates. |
| UpStream Security | It offers cloud based solutions for
Real time threat detection & prevention and uses Ai-ML to analyse data through predictive Analysis. |
| Intel Corporation | Intel acquired Mobilseye and now offers advanced driver-assistance systems (ADAS) and autonomous driving technologies. |
| Argus Cyber Security | Argus specializes in embedded cybersecurity solutions for connected and autonomous vehicles. |
| Cybellum | Cybellum focuses on vulnerability assessment and cyber forensics. Their Top Clients include Jaguar, Land Rover, Faurecia. |
| Symantec | Symantec provides tailor-made automotive cybersecurity solutions |
| GuardKnox | This company provides cybersecurity hardware solutions for end to end protection for connected vehicles.Its SNO i.e. Secure Network Orchestrator protects all electronic control units. |
| Karamba Security | Karamba provides an automotive cybersecurity solution for IoT and autonomous vehicles and offers solutions to protect connected devices and cars through security of the external controllers |
| Nvidia | Nvidia uses AI-powered data processors and chips to operate and protect self-driving cars. |
| Intertrust | It makes products that help personalize drivers cybersecurity needs and overall experience. |
| VisualThreat | A connected automobile security company that provides vehicle firewall and OTA updates. |
| Bosch Limited | Another giant that is actively involved in developing and deploying cybersecurity solutions for connected vehicles
and Lays major focus on OTA updates and Vehicle Control Unit. |
Conclusion
We witnessed the significance of automotive cybersecurity and its effect on the modern automobile industry. With this substantial market, an increasing number of companies are entering it, with the US playing a significant role. Prominent companies like Upstream Security, Cybllum, and Intel are working on more innovative solutions to tackle issues and develop a functional and reliable automotive ecosystem. The need became apparent as data breaches increased and cybercriminals were able to identify weaknesses in the ecosystem.